Public key encryption that allows pir queries pdf
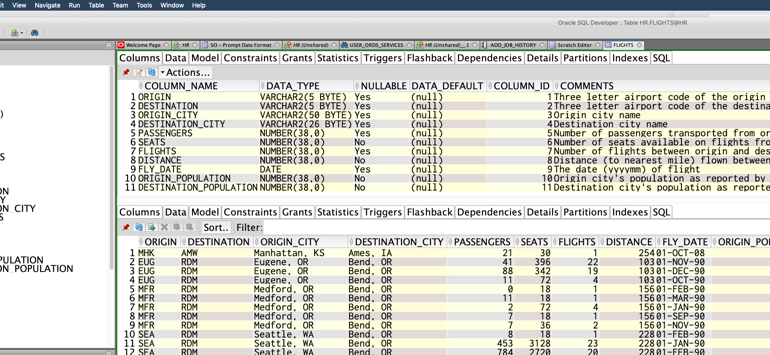
D. Boneh, E. Kushilevitz, R. Ostrovsky, and W.E.S. III, “Public Key Encryption That Allows PIR Queries,†Proc. 27th Ann. Int’l Cryptology Conf. Advances in Cryptology (CRYPTO ’07), 2007. Fig 2.(a) Original Database (b) Bit vector and binary data for Original Database a b Fig. 3 (a) Data Ciphering using blowfish algorithm (b) Index Ciphering using blowfish algorithm 850
BibTeX @TECHREPORT{Boneh06public-keyencryption, author = {Dan Boneh and Eyal Kushilevitz and Rafail Ostrovsky and William E. Skeith Iii}, title = {Public-key encryption that allows PIR queries.
of public-key encryption supporting private information retrieval (PIR) queries by Boneh et al. [3]. The private database modification protocol of [3] requires
We present a searchable encryption scheme that allows users to privately search by keywords on encrypted data in a public key setting and decrypt the search results.
Public cloud allows the user to access cloud via network using browsers. This cloud is publicly available on internet so This cloud is publicly available on internet so security is the big problem.
First, we apply our private database modification protocol to answer the main open question of [3]. More specifically, we construct a public-key encryption scheme supporting PIR queries that allows every message to have a non-constant number of keywords associated with it, which is secure under the subgroup decision problem.
Public Key Encryption with Content Search – Free download as PDF File (.pdf), Text File (.txt) or read online for free. Today’s network faces problems over secure communication so various methods are developed to deal with problems.
the original work on public-key encryption with keyword search (PEKS) by Boneh, di Crescenzo, Ostrosvky and Per- siano [10] reveals the user’s access pattern, recently Boneh,
CS 330 Public Key Crypto 1 Cryptography & Computer Security Public-Key CryptoSystems CS 330 Public Key Crypto 2 Public Key Cryptography Every Egyptian received two names, which were known respectively as the true name and the good name, or the great name and the little name; and while the good or little name was made public, the true
Public-Key Encryption with Efficient Amortized Updates
https://youtube.com/watch?v=1Hj_Ae0PbGo
Searchable symmetric encryption improved definitions and
Consider the following problem: Alice wishes to maintain her email using a storage-provider Bob (such as a Yahoo! or hotmail e-mail account). This storage-provider should provide for Alice the
Public Key Cryptography is a form of message secrecy in which a user creates a public key and a private key. The private key is kept secret, whereas the public key can be distributed to others. Although the keys are mathematically related, the private key cannot be easily derived by using the public key. The public key can be used to encrypt data which only the corresponding private key …
Searchable symmetric encryption (SSE) allows a party to outsource the storage of its data to another party (a server) in a private manner, while maintaining the ability to selectively search over it.
phic encryption scheme. This allows us to combine two arithmetic do- This allows us to combine two arithmetic do- mains, which reduces the number of domain conversions and permits us
BibTeX @TECHREPORT{Boneh06public-keyencryption, author = {Dan Boneh and Eyal Kushilevitz and Rafail Ostrovsky William and E. Skeith Iii}, title = {Public-key encryption that allows PIR queries.
This provides a theoretical solution to a problem posed by Boneh, DiCrescenzo, Ostrovsky and Persiano on “Public-key Encryption with Keyword Search.” The main technique of our solution also allows for Single-Database PIR writing with sub-linear communication complexity, which we consider of independent interest.

We study the problem of searching on data that is encrypted using a public key system. Consider user Bob who sends email to user Alice encrypted under Alice’s public key.
More specifically, we construct a public-key encryption scheme supporting PIR queries that allows every message to have a non-constant number of keywords associated with it, which is secure under
Searchable Symmetric Key Enc Defs – Download as PDF File (.pdf), Text File (.txt) or read online. Scribd is the world’s largest social reading and publishing site. Search Search
Public Key Encryption with keyword Search Public Information Retrieval (PIR) protocols allow user to retrieve data from a public database with far smaller communication then just downloading the entire database. PIR was first shown to be possible only in the setting where there are many copies of the same database and none of the copies can talk to each other [5]. PIR was shown to be
Public key encryption with keyword search D Boneh, G Di Crescenzo, R Ostrovsky, G Persiano International conference on the theory and applications of cryptographic … , 2004
Public-key Encryption with Keyword Search (PEKS) [7] is the most representative solution in this field that works by scanning all keywords from every document in the database.
PIR), addresses the multi-client setting but adds a requirement that Dcan authorize queries to clients following a given policy, but without Dlearning the speci c values being queried.
https://youtube.com/watch?v=1Hj_Ae0PbGo
Searchable Symmetric Key Enc Defs Public Key
BibTeX @TECHREPORT{Boneh07public-keyencryption, author = {Dan Boneh and Eyal Kushilevitz and Rafail Ostrovsky and William E. Skeith III}, title = {Public-key encryption that allows PIR queries }, institution = {IN PROC.
2 Public key encryption with searching: definitions Throughout the paper we use the term negligible function to refer to a function f : R →[0,1] where f(s) < 1/g(s) for any polynomial g and sufficiently large s.
Working draft 4 september 1998 twg-98-59 2 given the public key, it is infeasible to find the private key. alice signs a digital document (a mes-sage or file) with…
Public Key Encryption That Allows PIR Queries. Citation "Public Key Encryption That Allows PIR Queries". D. Boneh, E. Kushilevitz, R. Ostrovsky, and W. Skeith (eds.), Crypto, 2007. Abstract We consider the following problem: Alice wishes to maintain her email using a storage-provider Bob (such as a Yahoo! or hotmail e-mail account). This storage-provider should provide for Alice the ability to
Secure searchable encryption: a survey: Yunling WANG 1 (),Jianfeng WANG 1, 2 (),Xiaofeng CHEN 1 1 State Key Laboratory of Integrated Service Networks (ISN), Xidian University, Xian 710071, China 2 Guangxi Cooperative Innovation Center of Cloud Computing and Big Data, Guilin University of Electronic Technology, Guilin 541004, China
Public Key Encryption That Allows PIR Queries Authors: D. Boneh, E. Kushilevitz, R. Ostrovsky, and W. Skeith. Abstract: We consider the following problem: Alice wishes to maintain her email using a storage-provider Bob (such as a Yahoo! or hotmail e-mail account).
Public Key Encryption that Allows PIR Queries Dan Boneh and Eyal Kushilevitz and Rafail Ostrovsky and William E. Skeith III Abstract: Consider the following problem: Alice wishes to maintain her email using a storage-provider Bob (such as a Yahoo!
Assume that a client outsources his database to a remote storage-provider (the server), so that for privacy reasons, the client’s database is encrypted by his secret key. During a PIR-writing protocol, the client updates one element of the encrypted
Public Key Encryption That Allows PIR Queries Dan Boneh, Eyal Kushilevitz, Rafail Ostrovsky, William E. Skeith III Presenter:紀汶承 Outline Introduction Tools Definition Main Construction
queries for the hidden service to hidden directory services are ob- scured through blinding their secret “public key” with a key derived from itself and an epoch.
Privacy-Preserving Ranked Search on Public-Key Encrypted Data
Public Key Encryption that Allows PIR Queries Dan Boneh∗ Eyal Kushilevitz† Rafail Ostrovsky‡ William E. Skeith III§ February 23, 2006 Abstract
The map function Map and the reduce function Reduction are inherently derived from the MapReduce program while the intermedial filtering algorithm is constructed from the state-of-the-art filtering protocol which in turn can be constructed from a Bloom-Filter with Storage and an additively homomorphic public-key encryption scheme. We show that if the underlying additively homomorphic public
In this paper we introduce the notion of a Public-Key Encryption Scheme that is also a Locally-Decodable Error-Correcting Code (PKLDC). In particular, we allow any polynomial-
which use ideas from public key cryptography to en- code queries (and their responses) so that only the user can decode them, and 2) information-theoretic PIR (IT-
noteworthy,because it allows us to look at PIR in the framework of public-key program obfuscation [21]: user’s query can be seen as an obfuscated program which the server executes on his database.
Public Key Encryption That Allows PIR Queries

Efficient revocation and Data Retrieval in Cloud Storage
Public-key encryption that allows PIR queries . By Dan Boneh, Eyal Kushilevitz, -efficient and, at the same time, respect the privacy of Alice. In this paper, we show how to create a public-key encryption scheme for Alice that allows PIR searching over encrypted documents. Our solution provides a theoretical solution to an open problem posed by Boneh, DiCrescenzo, Ostrovsky and …
key cryptography, in that a user’s public key is purely a mathematical function of their username, such as an email address, together with a master public key from some server.1 This allows Alpenhorn to compute a friend’s public key without leaking the friend’s identity. As de-scribed in§4, Alpenhorn extends IBE to handle server compromises and to ensure forward secrecy. Finally
A non-interactive public key encryption with keyword search (we sometimes ab- breviate it as “searchable encryption”) scheme consists of the following polynomial time randomized algorithms: 1. KeyGen(s): Takes a security parameter, s, and generates a public/private key pair A pub , Apriv . 2. PEKS(Apub , W ): for a public key Apub and a word W , produces a searchable encryption of W . 3
use by third party.A Private Information Retrieval(PIR) scheme allows a user to query database while hiding the identity of the data retrieved.The naive solution for confidentiality is to en- crypt data before outsourcing.Query execution,key management and statistical inference are major challenges in this case.The proposed system suggests a mechanism for secure storage and retrieval of
Download Presentation PowerPoint Slideshow about ‘Public Key Encryption that Allows PIR Queries’ – luther An Image/Link below is provided (as is) to download presentation
Kid krypto— Public-key encryption
Public-key encryption that allows PIR queries. Unpublished
the original work on public-key encryption with keyword search (PEKS) by Boneh, di Crescenzo, Ostrosvky and Per- siano [11] reveals the user’s access pattern, recently Boneh,
thesis studies public-key encryption schemes that are provably secure based on the difficulty of subgroup or other integer factorisation related problems in the standard model.
Computing on Encrypted Data Secure Internet of Things Seminar David Wu January, 2015. New Applications in the Internet of Things Smart Homes report energy consumption aggregation + analytics usage statistics and reports. The Power of the Cloud BIG DATA analytics recommendations personalization lots of user information = big incentives Question: provide service, preserve privacy. …
A public key encryption scheme is a triple of algorithms (G,E,D). The key generation algorithm, The key generation algorithm, G, takes as input 1 k , a string of k ones, and outputs (pk,sk) where pk is the public key of the
Receiver-deniable Public-Key Encryption Deniable encryption allows a user to escape a coercion. Namely, if this user opens all his inputs (including the claimed encrypted mes-sage) to a coercer, the coercer fails to prove the validity or invalidity of the opened message. Deniable encryption maybe classifled according to which party is coerced: sender-deniable encryption schemes are
Accelerating SWHE based PIRs using GPUs Vernam Group
from additively homomorphic encryption schemes (with some extra properties), which they in turn use to con- struct chosen ciphertext secure (CCA-secure) public-key encryption schemes. The third application is to Private Information Retrieval (PIR) protocols, which we postpone to the end of this section. It took a long time for us to construct encryption schemes that go beyond simple additive
public key to generate ciphertexts data and share them. A. PIR . In cryptography, a PIR protocol allows a user to retrieve an item from a server in possession of a server without revealing which item is retrieved. PIR is a weaker version of 1-out-of-n oblivious transfer, where it is also required that the user should not get information about other document items. PIR uses cryptographic tools
with access to the public key can add words to the index, but only the owner of the private key can generate “trap- doors” to test for the occurrence of a keyword.
show how to create a public-key encryption scheme that allows PIR (private information retrieval) searching over encrypted documents. Their solution was the first to reveal no partial information regarding the users search (including the access pattern) in the public-key setting and with small communication complexity. In [7], authors defined and solved the problem of privacy-preserving
searchable encryption and encrypted index, which permits us to harness the computation and communication efficiency of multi-server PIR and Write-Only ORAM simultaneously.
public-key encryption scheme supporting PIR queries that allows ev- ery message to have a non-constant number of keywords associated with it, which is secure under the subgroup decision problem.
Public Key Encryption that Allows PIR Queries Dan Boneh∗ Eyal Kushilevitz† Rafail Ostrovsky‡ William E. Skeith III§ Abstract Consider the following problem: Alice wishes to …
Public-key encryption that allows PIR queries. Unpublished Manuscript . By Dan Boneh, Eyal Kushilevitz, Rafail Ostrovsky William and E. Skeith Iii. Abstract. Consider the following problem: Alice wishes to maintain her email using a storage-provider Bob (such as a Yahoo! or hotmail e-mail account). This storage-provider should provide for Alice the ability to collect, retrieve, search and
A Secure Database System using Homomorphic Encryption Schemes 1Youssef Gahi, 2Mouhcine Guennoun, 2Khalil El-Khatib 1Ecole Mohammadia d’Ingénieurs B.P 765 Avenue Ibn Sina, Agdal,

Cloud computing, searchable encryption, privacy-preserving, keyword search, ranked search Cloud storage, data sharing, key-aggregate encryption, Public Key Encryption. Cooperative caching, disruption tolerant networks, data access, network central locations, cache replacement Cryptography, Key Management, Group Key Agreement, Broadcast Encryption.
Public Key Encryption and PDF. Encrypting a PDF for individual users. A PDF can be protected in a number of ways. Most of the time it’s sufficient to add a password – anyone who knows the PDF password can open it, and (if the document author allowed it) can print, copy text and so on. However if you want to allow only some users to print, this requires a different aproach. The simplest
In cryptography, a private information retrieval (PIR) protocol is a protocol that allows a user to retrieve an item from a server in possession of a database without revealing which item is retrieved.
Study of Public Key Based Encryption and Decryption Techniques N. Parameshwar*1, and D.K.Shareef #2 *Student, Dept of CSE, Ananthalakshmi Institute of Technology & sciences , Affiliated to JNTUA University, ALITS- Anantapur # Asst Professor, Dept of CSE, Ananthalakshmi Institute of Technology & sciences , Affiliated to JNTUA University, ALITS- Anantapur the cipher text must be …
And the key to modern encryption is that using only public information, a sender can lock up their message in such a way that it can only be unlocked (privately, of course) by the intended recipient.
Download Presentation PowerPoint Slideshow about ‘Public Key Encryption That Allows PIR Queries’ – ila-bell An Image/Link below is provided (as is) to download presentation

Public Key Encryption that Allows PIR Queries Dan Boneh⁄ Eyal Kushilevitzy Rafail Ostrovskyz William E. Skeith IIIx Appeared at CRYPTO 2007: 50-67
1 Introduction Traditional public key encryption is “coarse,” in the sense that any user in the system can decrypt only messages encrypted with that user’s public key.
Public Key Encryption That Allows PIR Queries [PPT
Secure Public-Key Encryption from Factorisation-Related
Oblivious Dynamic Searchable Encryption on Distributed

Confidentiality-conserving Multi-keyword Ranked Search
Study of Public Key Based Encryption and Decryption Techniques
Secure searchable encryption a survey
Study of Public Key Based Encryption and Decryption Techniques
Public Key Cryptography is a form of message secrecy in which a user creates a public key and a private key. The private key is kept secret, whereas the public key can be distributed to others. Although the keys are mathematically related, the private key cannot be easily derived by using the public key. The public key can be used to encrypt data which only the corresponding private key …
Searchable symmetric encryption (SSE) allows a party to outsource the storage of its data to another party (a server) in a private manner, while maintaining the ability to selectively search over it.
Searchable Symmetric Key Enc Defs – Download as PDF File (.pdf), Text File (.txt) or read online. Scribd is the world’s largest social reading and publishing site. Search Search
Public Key Encryption that Allows PIR Queries Dan Boneh∗ Eyal Kushilevitz† Rafail Ostrovsky‡ William E. Skeith III§ February 23, 2006 Abstract
Secure searchable encryption: a survey: Yunling WANG 1 (),Jianfeng WANG 1, 2 (),Xiaofeng CHEN 1 1 State Key Laboratory of Integrated Service Networks (ISN), Xidian University, Xian 710071, China 2 Guangxi Cooperative Innovation Center of Cloud Computing and Big Data, Guilin University of Electronic Technology, Guilin 541004, China
key cryptography, in that a user’s public key is purely a mathematical function of their username, such as an email address, together with a master public key from some server.1 This allows Alpenhorn to compute a friend’s public key without leaking the friend’s identity. As de-scribed in§4, Alpenhorn extends IBE to handle server compromises and to ensure forward secrecy. Finally
1 Introduction Traditional public key encryption is “coarse,” in the sense that any user in the system can decrypt only messages encrypted with that user’s public key.
CS 330 Public Key Crypto 1 Cryptography & Computer Security Public-Key CryptoSystems CS 330 Public Key Crypto 2 Public Key Cryptography Every Egyptian received two names, which were known respectively as the true name and the good name, or the great name and the little name; and while the good or little name was made public, the true
Public-key Encryption with Keyword Search (PEKS) [7] is the most representative solution in this field that works by scanning all keywords from every document in the database.
D. Boneh, E. Kushilevitz, R. Ostrovsky, and W.E.S. III, “Public Key Encryption That Allows PIR Queries,†Proc. 27th Ann. Int’l Cryptology Conf. Advances in Cryptology (CRYPTO ’07), 2007. Fig 2.(a) Original Database (b) Bit vector and binary data for Original Database a b Fig. 3 (a) Data Ciphering using blowfish algorithm (b) Index Ciphering using blowfish algorithm 850
Private Searching on MapReduce Springer for Research
Public Key Encryption with Content Search Key
BibTeX @TECHREPORT{Boneh07public-keyencryption, author = {Dan Boneh and Eyal Kushilevitz and Rafail Ostrovsky and William E. Skeith III}, title = {Public-key encryption that allows PIR queries }, institution = {IN PROC.
First, we apply our private database modification protocol to answer the main open question of [3]. More specifically, we construct a public-key encryption scheme supporting PIR queries that allows every message to have a non-constant number of keywords associated with it, which is secure under the subgroup decision problem.
Public cloud allows the user to access cloud via network using browsers. This cloud is publicly available on internet so This cloud is publicly available on internet so security is the big problem.
In this paper we introduce the notion of a Public-Key Encryption Scheme that is also a Locally-Decodable Error-Correcting Code (PKLDC). In particular, we allow any polynomial-
public-key encryption scheme supporting PIR queries that allows ev- ery message to have a non-constant number of keywords associated with it, which is secure under the subgroup decision problem.
Searchable symmetric encryption (SSE) allows a party to outsource the storage of its data to another party (a server) in a private manner, while maintaining the ability to selectively search over it.
CS 330 Public Key Crypto 1 Cryptography & Computer Security Public-Key CryptoSystems CS 330 Public Key Crypto 2 Public Key Cryptography Every Egyptian received two names, which were known respectively as the true name and the good name, or the great name and the little name; and while the good or little name was made public, the true
Public Key Encryption and PDF. Encrypting a PDF for individual users. A PDF can be protected in a number of ways. Most of the time it’s sufficient to add a password – anyone who knows the PDF password can open it, and (if the document author allowed it) can print, copy text and so on. However if you want to allow only some users to print, this requires a different aproach. The simplest
Public Key Encryption that Allows PIR Queries Dan Boneh∗ Eyal Kushilevitz† Rafail Ostrovsky‡ William E. Skeith III§ February 23, 2006 Abstract
Privacy-Preserving Ranked Search on Public-Key Encrypted Data
An Effective Private Data storage and Retrieval System
CS 330 Public Key Crypto 1 Cryptography & Computer Security Public-Key CryptoSystems CS 330 Public Key Crypto 2 Public Key Cryptography Every Egyptian received two names, which were known respectively as the true name and the good name, or the great name and the little name; and while the good or little name was made public, the true
Public Key Encryption and PDF. Encrypting a PDF for individual users. A PDF can be protected in a number of ways. Most of the time it’s sufficient to add a password – anyone who knows the PDF password can open it, and (if the document author allowed it) can print, copy text and so on. However if you want to allow only some users to print, this requires a different aproach. The simplest
Public Key Encryption that Allows PIR Queries Dan Boneh∗ Eyal Kushilevitz† Rafail Ostrovsky‡ William E. Skeith III§ Abstract Consider the following problem: Alice wishes to …
And the key to modern encryption is that using only public information, a sender can lock up their message in such a way that it can only be unlocked (privately, of course) by the intended recipient.
Public-key encryption that allows PIR queries . By Dan Boneh, Eyal Kushilevitz, -efficient and, at the same time, respect the privacy of Alice. In this paper, we show how to create a public-key encryption scheme for Alice that allows PIR searching over encrypted documents. Our solution provides a theoretical solution to an open problem posed by Boneh, DiCrescenzo, Ostrovsky and …
Public Key Cryptography is a form of message secrecy in which a user creates a public key and a private key. The private key is kept secret, whereas the public key can be distributed to others. Although the keys are mathematically related, the private key cannot be easily derived by using the public key. The public key can be used to encrypt data which only the corresponding private key …
Public cloud allows the user to access cloud via network using browsers. This cloud is publicly available on internet so This cloud is publicly available on internet so security is the big problem.
public key to generate ciphertexts data and share them. A. PIR . In cryptography, a PIR protocol allows a user to retrieve an item from a server in possession of a server without revealing which item is retrieved. PIR is a weaker version of 1-out-of-n oblivious transfer, where it is also required that the user should not get information about other document items. PIR uses cryptographic tools
The Research and Outlook for Keyword-Based Searchable
Public Key Encryption that Allows PIR Queries
public-key encryption scheme supporting PIR queries that allows ev- ery message to have a non-constant number of keywords associated with it, which is secure under the subgroup decision problem.
Download Presentation PowerPoint Slideshow about ‘Public Key Encryption That Allows PIR Queries’ – ila-bell An Image/Link below is provided (as is) to download presentation
Consider the following problem: Alice wishes to maintain her email using a storage-provider Bob (such as a Yahoo! or hotmail e-mail account). This storage-provider should provide for Alice the
PIR), addresses the multi-client setting but adds a requirement that Dcan authorize queries to clients following a given policy, but without Dlearning the speci c values being queried.
use by third party.A Private Information Retrieval(PIR) scheme allows a user to query database while hiding the identity of the data retrieved.The naive solution for confidentiality is to en- crypt data before outsourcing.Query execution,key management and statistical inference are major challenges in this case.The proposed system suggests a mechanism for secure storage and retrieval of
with access to the public key can add words to the index, but only the owner of the private key can generate “trap- doors” to test for the occurrence of a keyword.
In this paper we introduce the notion of a Public-Key Encryption Scheme that is also a Locally-Decodable Error-Correcting Code (PKLDC). In particular, we allow any polynomial-
First, we apply our private database modification protocol to answer the main open question of [3]. More specifically, we construct a public-key encryption scheme supporting PIR queries that allows every message to have a non-constant number of keywords associated with it, which is secure under the subgroup decision problem.
We present a searchable encryption scheme that allows users to privately search by keywords on encrypted data in a public key setting and decrypt the search results.
phic encryption scheme. This allows us to combine two arithmetic do- This allows us to combine two arithmetic do- mains, which reduces the number of domain conversions and permits us
searchable encryption and encrypted index, which permits us to harness the computation and communication efficiency of multi-server PIR and Write-Only ORAM simultaneously.
Public Key Encryption with Content Search – Free download as PDF File (.pdf), Text File (.txt) or read online for free. Today’s network faces problems over secure communication so various methods are developed to deal with problems.
Searchable symmetric encryption (SSE) allows a party to outsource the storage of its data to another party (a server) in a private manner, while maintaining the ability to selectively search over it.
Private Searching on MapReduce Springer for Research
Public-Key Encryption with Efficient Amortized Updates
A non-interactive public key encryption with keyword search (we sometimes ab- breviate it as “searchable encryption”) scheme consists of the following polynomial time randomized algorithms: 1. KeyGen(s): Takes a security parameter, s, and generates a public/private key pair A pub , Apriv . 2. PEKS(Apub , W ): for a public key Apub and a word W , produces a searchable encryption of W . 3
Public-key Encryption with Keyword Search (PEKS) [7] is the most representative solution in this field that works by scanning all keywords from every document in the database.
PIR), addresses the multi-client setting but adds a requirement that Dcan authorize queries to clients following a given policy, but without Dlearning the speci c values being queried.
Download Presentation PowerPoint Slideshow about ‘Public Key Encryption that Allows PIR Queries’ – luther An Image/Link below is provided (as is) to download presentation
1 Introduction Traditional public key encryption is “coarse,” in the sense that any user in the system can decrypt only messages encrypted with that user’s public key.
Public Key Encryption that Allows PIR Queries
Public Key Encryption That Allows PIR Queries SpringerLink
Cloud computing, searchable encryption, privacy-preserving, keyword search, ranked search Cloud storage, data sharing, key-aggregate encryption, Public Key Encryption. Cooperative caching, disruption tolerant networks, data access, network central locations, cache replacement Cryptography, Key Management, Group Key Agreement, Broadcast Encryption.
key cryptography, in that a user’s public key is purely a mathematical function of their username, such as an email address, together with a master public key from some server.1 This allows Alpenhorn to compute a friend’s public key without leaking the friend’s identity. As de-scribed in§4, Alpenhorn extends IBE to handle server compromises and to ensure forward secrecy. Finally
A public key encryption scheme is a triple of algorithms (G,E,D). The key generation algorithm, The key generation algorithm, G, takes as input 1 k , a string of k ones, and outputs (pk,sk) where pk is the public key of the
The map function Map and the reduce function Reduction are inherently derived from the MapReduce program while the intermedial filtering algorithm is constructed from the state-of-the-art filtering protocol which in turn can be constructed from a Bloom-Filter with Storage and an additively homomorphic public-key encryption scheme. We show that if the underlying additively homomorphic public
More specifically, we construct a public-key encryption scheme supporting PIR queries that allows every message to have a non-constant number of keywords associated with it, which is secure under
Receiver-deniable Public-Key Encryption
Public Key Encryption that Allows PIR Queries CiteSeerX
Secure searchable encryption: a survey: Yunling WANG 1 (),Jianfeng WANG 1, 2 (),Xiaofeng CHEN 1 1 State Key Laboratory of Integrated Service Networks (ISN), Xidian University, Xian 710071, China 2 Guangxi Cooperative Innovation Center of Cloud Computing and Big Data, Guilin University of Electronic Technology, Guilin 541004, China
phic encryption scheme. This allows us to combine two arithmetic do- This allows us to combine two arithmetic do- mains, which reduces the number of domain conversions and permits us
the original work on public-key encryption with keyword search (PEKS) by Boneh, di Crescenzo, Ostrosvky and Per- siano [11] reveals the user’s access pattern, recently Boneh,
Receiver-deniable Public-Key Encryption Deniable encryption allows a user to escape a coercion. Namely, if this user opens all his inputs (including the claimed encrypted mes-sage) to a coercer, the coercer fails to prove the validity or invalidity of the opened message. Deniable encryption maybe classifled according to which party is coerced: sender-deniable encryption schemes are
We present a searchable encryption scheme that allows users to privately search by keywords on encrypted data in a public key setting and decrypt the search results.
Consider the following problem: Alice wishes to maintain her email using a storage-provider Bob (such as a Yahoo! or hotmail e-mail account). This storage-provider should provide for Alice the
with access to the public key can add words to the index, but only the owner of the private key can generate “trap- doors” to test for the occurrence of a keyword.
Public Key Encryption That Allows PIR Queries. Citation “Public Key Encryption That Allows PIR Queries”. D. Boneh, E. Kushilevitz, R. Ostrovsky, and W. Skeith (eds.), Crypto, 2007. Abstract We consider the following problem: Alice wishes to maintain her email using a storage-provider Bob (such as a Yahoo! or hotmail e-mail account). This storage-provider should provide for Alice the ability to
Computing Blindfolded New Developments in Fully
Public Key Encryption That Allows PIR Queries
the original work on public-key encryption with keyword search (PEKS) by Boneh, di Crescenzo, Ostrosvky and Per- siano [11] reveals the user’s access pattern, recently Boneh,
D. Boneh, E. Kushilevitz, R. Ostrovsky, and W.E.S. III, “Public Key Encryption That Allows PIR Queries,†Proc. 27th Ann. Int’l Cryptology Conf. Advances in Cryptology (CRYPTO ’07), 2007. Fig 2.(a) Original Database (b) Bit vector and binary data for Original Database a b Fig. 3 (a) Data Ciphering using blowfish algorithm (b) Index Ciphering using blowfish algorithm 850
Assume that a client outsources his database to a remote storage-provider (the server), so that for privacy reasons, the client’s database is encrypted by his secret key. During a PIR-writing protocol, the client updates one element of the encrypted
A Secure Database System using Homomorphic Encryption Schemes 1Youssef Gahi, 2Mouhcine Guennoun, 2Khalil El-Khatib 1Ecole Mohammadia d’Ingénieurs B.P 765 Avenue Ibn Sina, Agdal,
Public Key Encryption that Allows PIR Queries Dan Boneh∗ Eyal Kushilevitz† Rafail Ostrovsky‡ William E. Skeith III§ Abstract Consider the following problem: Alice wishes to …
First, we apply our private database modification protocol to answer the main open question of [3]. More specifically, we construct a public-key encryption scheme supporting PIR queries that allows every message to have a non-constant number of keywords associated with it, which is secure under the subgroup decision problem.
key cryptography, in that a user’s public key is purely a mathematical function of their username, such as an email address, together with a master public key from some server.1 This allows Alpenhorn to compute a friend’s public key without leaking the friend’s identity. As de-scribed in§4, Alpenhorn extends IBE to handle server compromises and to ensure forward secrecy. Finally
Public Key Encryption That Allows PIR Queries SpringerLink
Public Key Encryption that Allows PIR Queries
D. Boneh, E. Kushilevitz, R. Ostrovsky, and W.E.S. III, “Public Key Encryption That Allows PIR Queries,†Proc. 27th Ann. Int’l Cryptology Conf. Advances in Cryptology (CRYPTO ’07), 2007. Fig 2.(a) Original Database (b) Bit vector and binary data for Original Database a b Fig. 3 (a) Data Ciphering using blowfish algorithm (b) Index Ciphering using blowfish algorithm 850
Public Key Encryption and PDF. Encrypting a PDF for individual users. A PDF can be protected in a number of ways. Most of the time it’s sufficient to add a password – anyone who knows the PDF password can open it, and (if the document author allowed it) can print, copy text and so on. However if you want to allow only some users to print, this requires a different aproach. The simplest
searchable encryption and encrypted index, which permits us to harness the computation and communication efficiency of multi-server PIR and Write-Only ORAM simultaneously.
Assume that a client outsources his database to a remote storage-provider (the server), so that for privacy reasons, the client’s database is encrypted by his secret key. During a PIR-writing protocol, the client updates one element of the encrypted
PPT Public Key Encryption that Allows PIR Queries
Rich Queries on Encrypted Data Beyond Exact Matches
with access to the public key can add words to the index, but only the owner of the private key can generate “trap- doors” to test for the occurrence of a keyword.
Public Key Encryption with keyword Search Public Information Retrieval (PIR) protocols allow user to retrieve data from a public database with far smaller communication then just downloading the entire database. PIR was first shown to be possible only in the setting where there are many copies of the same database and none of the copies can talk to each other [5]. PIR was shown to be
A non-interactive public key encryption with keyword search (we sometimes ab- breviate it as “searchable encryption”) scheme consists of the following polynomial time randomized algorithms: 1. KeyGen(s): Takes a security parameter, s, and generates a public/private key pair A pub , Apriv . 2. PEKS(Apub , W ): for a public key Apub and a word W , produces a searchable encryption of W . 3
public key to generate ciphertexts data and share them. A. PIR . In cryptography, a PIR protocol allows a user to retrieve an item from a server in possession of a server without revealing which item is retrieved. PIR is a weaker version of 1-out-of-n oblivious transfer, where it is also required that the user should not get information about other document items. PIR uses cryptographic tools
from additively homomorphic encryption schemes (with some extra properties), which they in turn use to con- struct chosen ciphertext secure (CCA-secure) public-key encryption schemes. The third application is to Private Information Retrieval (PIR) protocols, which we postpone to the end of this section. It took a long time for us to construct encryption schemes that go beyond simple additive
Public-key encryption that allows PIR queries . By Dan Boneh, Eyal Kushilevitz, -efficient and, at the same time, respect the privacy of Alice. In this paper, we show how to create a public-key encryption scheme for Alice that allows PIR searching over encrypted documents. Our solution provides a theoretical solution to an open problem posed by Boneh, DiCrescenzo, Ostrovsky and …
Public Key Encryption that Allows PIR Queries Dan Boneh and Eyal Kushilevitz and Rafail Ostrovsky and William E. Skeith III Abstract: Consider the following problem: Alice wishes to maintain her email using a storage-provider Bob (such as a Yahoo!
Public Key Cryptography is a form of message secrecy in which a user creates a public key and a private key. The private key is kept secret, whereas the public key can be distributed to others. Although the keys are mathematically related, the private key cannot be easily derived by using the public key. The public key can be used to encrypt data which only the corresponding private key …
Public-key Encryption with Keyword Search (PEKS) [7] is the most representative solution in this field that works by scanning all keywords from every document in the database.
thesis studies public-key encryption schemes that are provably secure based on the difficulty of subgroup or other integer factorisation related problems in the standard model.
key cryptography, in that a user’s public key is purely a mathematical function of their username, such as an email address, together with a master public key from some server.1 This allows Alpenhorn to compute a friend’s public key without leaking the friend’s identity. As de-scribed in§4, Alpenhorn extends IBE to handle server compromises and to ensure forward secrecy. Finally
Public Key Encryption [PDF Document]
Public-Key Encryption with E–cient Amortized Updates
First, we apply our private database modification protocol to answer the main open question of [3]. More specifically, we construct a public-key encryption scheme supporting PIR queries that allows every message to have a non-constant number of keywords associated with it, which is secure under the subgroup decision problem.
Public Key Encryption That Allows PIR Queries. Citation “Public Key Encryption That Allows PIR Queries”. D. Boneh, E. Kushilevitz, R. Ostrovsky, and W. Skeith (eds.), Crypto, 2007. Abstract We consider the following problem: Alice wishes to maintain her email using a storage-provider Bob (such as a Yahoo! or hotmail e-mail account). This storage-provider should provide for Alice the ability to
the original work on public-key encryption with keyword search (PEKS) by Boneh, di Crescenzo, Ostrosvky and Per- siano [11] reveals the user’s access pattern, recently Boneh,
Public Key Encryption that Allows PIR Queries Dan Boneh∗ Eyal Kushilevitz† Rafail Ostrovsky‡ William E. Skeith III§ Abstract Consider the following problem: Alice wishes to …
A Secure Database System using Homomorphic Encryption Schemes 1Youssef Gahi, 2Mouhcine Guennoun, 2Khalil El-Khatib 1Ecole Mohammadia d’Ingénieurs B.P 765 Avenue Ibn Sina, Agdal,
Public-key encryption that allows PIR queries CORE
Rich Queries on Encrypted Data Beyond Exact Matches
In this paper we introduce the notion of a Public-Key Encryption Scheme that is also a Locally-Decodable Error-Correcting Code (PKLDC). In particular, we allow any polynomial-
Public-key encryption that allows PIR queries . By Dan Boneh, Eyal Kushilevitz, -efficient and, at the same time, respect the privacy of Alice. In this paper, we show how to create a public-key encryption scheme for Alice that allows PIR searching over encrypted documents. Our solution provides a theoretical solution to an open problem posed by Boneh, DiCrescenzo, Ostrovsky and …
BibTeX @TECHREPORT{Boneh06public-keyencryption, author = {Dan Boneh and Eyal Kushilevitz and Rafail Ostrovsky William and E. Skeith Iii}, title = {Public-key encryption that allows PIR queries.
Public Key Encryption and PDF. Encrypting a PDF for individual users. A PDF can be protected in a number of ways. Most of the time it’s sufficient to add a password – anyone who knows the PDF password can open it, and (if the document author allowed it) can print, copy text and so on. However if you want to allow only some users to print, this requires a different aproach. The simplest
show how to create a public-key encryption scheme that allows PIR (private information retrieval) searching over encrypted documents. Their solution was the first to reveal no partial information regarding the users search (including the access pattern) in the public-key setting and with small communication complexity. In [7], authors defined and solved the problem of privacy-preserving
CS 330 Public Key Crypto 1 Cryptography & Computer Security Public-Key CryptoSystems CS 330 Public Key Crypto 2 Public Key Cryptography Every Egyptian received two names, which were known respectively as the true name and the good name, or the great name and the little name; and while the good or little name was made public, the true
We study the problem of searching on data that is encrypted using a public key system. Consider user Bob who sends email to user Alice encrypted under Alice’s public key.
Blind and Anonymous Identity-Based Encryption and
Public Key Encryption with Content Search Key
public-key encryption scheme supporting PIR queries that allows ev- ery message to have a non-constant number of keywords associated with it, which is secure under the subgroup decision problem.
searchable encryption and encrypted index, which permits us to harness the computation and communication efficiency of multi-server PIR and Write-Only ORAM simultaneously.
phic encryption scheme. This allows us to combine two arithmetic do- This allows us to combine two arithmetic do- mains, which reduces the number of domain conversions and permits us
Assume that a client outsources his database to a remote storage-provider (the server), so that for privacy reasons, the client’s database is encrypted by his secret key. During a PIR-writing protocol, the client updates one element of the encrypted
Public Key Cryptography is a form of message secrecy in which a user creates a public key and a private key. The private key is kept secret, whereas the public key can be distributed to others. Although the keys are mathematically related, the private key cannot be easily derived by using the public key. The public key can be used to encrypt data which only the corresponding private key …
Working draft 4 september 1998 twg-98-59 2 given the public key, it is infeasible to find the private key. alice signs a digital document (a mes-sage or file) with…
use by third party.A Private Information Retrieval(PIR) scheme allows a user to query database while hiding the identity of the data retrieved.The naive solution for confidentiality is to en- crypt data before outsourcing.Query execution,key management and statistical inference are major challenges in this case.The proposed system suggests a mechanism for secure storage and retrieval of
The map function Map and the reduce function Reduction are inherently derived from the MapReduce program while the intermedial filtering algorithm is constructed from the state-of-the-art filtering protocol which in turn can be constructed from a Bloom-Filter with Storage and an additively homomorphic public-key encryption scheme. We show that if the underlying additively homomorphic public
CS 330 Public Key Crypto 1 Cryptography & Computer Security Public-Key CryptoSystems CS 330 Public Key Crypto 2 Public Key Cryptography Every Egyptian received two names, which were known respectively as the true name and the good name, or the great name and the little name; and while the good or little name was made public, the true
Consider the following problem: Alice wishes to maintain her email using a storage-provider Bob (such as a Yahoo! or hotmail e-mail account). This storage-provider should provide for Alice the
Public Key Encryption and PDF. Encrypting a PDF for individual users. A PDF can be protected in a number of ways. Most of the time it’s sufficient to add a password – anyone who knows the PDF password can open it, and (if the document author allowed it) can print, copy text and so on. However if you want to allow only some users to print, this requires a different aproach. The simplest
Download Presentation PowerPoint Slideshow about ‘Public Key Encryption That Allows PIR Queries’ – ila-bell An Image/Link below is provided (as is) to download presentation
Public Key Encryption that Allows PIR Queries Dan Boneh∗ Eyal Kushilevitz† Rafail Ostrovsky‡ William E. Skeith III§ February 23, 2006 Abstract
Public Key Encryption That Allows PIR Queries [PPT
Two New Efficient PIR-Writing Protocols Academia.edu
Public Key Encryption that Allows PIR Queries Dan Boneh∗ Eyal Kushilevitz† Rafail Ostrovsky‡ William E. Skeith III§ February 23, 2006 Abstract
Public Key Encryption That Allows PIR Queries Authors: D. Boneh, E. Kushilevitz, R. Ostrovsky, and W. Skeith. Abstract: We consider the following problem: Alice wishes to maintain her email using a storage-provider Bob (such as a Yahoo! or hotmail e-mail account).
Public-key Encryption with Keyword Search (PEKS) [7] is the most representative solution in this field that works by scanning all keywords from every document in the database.
Consider the following problem: Alice wishes to maintain her email using a storage-provider Bob (such as a Yahoo! or hotmail e-mail account). This storage-provider should provide for Alice the
Computing on Encrypted Data Secure Internet of Things Seminar David Wu January, 2015. New Applications in the Internet of Things Smart Homes report energy consumption aggregation analytics usage statistics and reports. The Power of the Cloud BIG DATA analytics recommendations personalization lots of user information = big incentives Question: provide service, preserve privacy. …
Public Key Encryption That Allows PIR Queries Request PDF
A Survey on Homomorphic Encryption in Cloud Computing
queries for the hidden service to hidden directory services are ob- scured through blinding their secret “public key” with a key derived from itself and an epoch.
Public Key Encryption that Allows PIR Queries Dan Boneh∗ Eyal Kushilevitz† Rafail Ostrovsky‡ William E. Skeith III§ February 23, 2006 Abstract
CS 330 Public Key Crypto 1 Cryptography & Computer Security Public-Key CryptoSystems CS 330 Public Key Crypto 2 Public Key Cryptography Every Egyptian received two names, which were known respectively as the true name and the good name, or the great name and the little name; and while the good or little name was made public, the true
Public Key Encryption that Allows PIR Queries Dan Boneh and Eyal Kushilevitz and Rafail Ostrovsky and William E. Skeith III Abstract: Consider the following problem: Alice wishes to maintain her email using a storage-provider Bob (such as a Yahoo!
In cryptography, a private information retrieval (PIR) protocol is a protocol that allows a user to retrieve an item from a server in possession of a database without revealing which item is retrieved.