History of computer forensics pdf
History Description: Records websites visited by date and time. Details stored for each local user account. Records number of times visited (frequency).
Computer forensics is the task of recovering data that users have hidden or deleted,with the goal of ensuring that the recovered data is valid so that it can be used as evidence. The
Based on theory gained from the science and culture research domain, this paper considers the relationship between computer forensic science and culture. In order to develop a theoretical relationship between computer forensics and culture, this paper examines computer forensics …
The course will provide you a solid foundation of the theoretical and practical aspects of the different dimensions of cyber security, such as network security, software security, system security measures and models, information security, computer forensics, penetration testing and vulnerability assessment, risk and project management and knowledge of relevant standards and regulatory
Computer Forensics Seminar and PPT with pdf report: “Forensic computing is the process of determining, preserving, scrutinizing and presenting digital evidence in a manner that is legally acceptable.”(Rodney Mckemmish 1999). This page contains Computer Forensics Seminar and PPT with pdf …
number of new and improved computer forensic investigation processes have been developed. In this paper, we reviewed a few selected investigation processes that have been produced throughout the years and then identified the commonly shared processes. Hopefully, with the identification of the commonly shard process, it would make it easier for the new users to understand the processes and …
It is important to understand the history of computer forensics in order to understand how educational programs might be developed in this discipline. Media analysis was the child of law enforcement necessity. Computers were being found at crime scenes and investigators were eager to use this new source of information. The investigators sought out people to assist in making this latent form of
Computer evidences admitted in courts could be any file or fragment recovered from the storage devices such as email, browsing history, graphics, photographs, or application documents. These …
Digital Evidence and Computer Crime, Third Edition 6 CHAPTER 1: Foundations of Digital Forensics retain e-mail and other data as required by the Securities and Exchange Act of 1934 ( Securities and Exchange Commission, 2002 ). Digital evidence can be useful in a wide range of criminal investigations including homicides, sex offenses, missing persons, child abuse, drug dealing, fraud, …
The Evolution of Digital Forensics Page 3 This work is licensed under the Creative Commons Attribution-No Derivative Works 3.0 Unported License.
Computer crime investigation and computer forensics are also evolv- ing sciences that are affected by many exte rnal factors, such as continued advancements in technology, societal …
Digital evidence, computer forensics. digital forensics experts regarding applicability and acceptance of tools and techniques are all areas that will be probed in such threshold determinations of admissibility. To the extent that digital forensics is more art than science, and less based on standards, it may have trouble surviving such a challenge. 3. ADMISSIBILITY OF DIGITAL EVIDENCE If
OBJECTIVES • Computer Crime • Overview Of Digital Forensics – Description And History – Uses – Basic Procedures – Analysis • Small Scale Digital Devices (SSDD)
Computer Forensics – Past, Present and Future Derek Bem, Francine Feld, Ewa Huebner, Oscar Bem University of Western Sydney, Australia Abstract In this paper we examine the emergence and evolution of computer crime and computer forensics, as well as the crisis computer forensics is now facing. We propose new directions and approaches which better reflect the current objectives of this
His research interests include Computer and Mobile Forensics, Information Security and Cloud Computing. He holds a MS in Electronic Engineering from Polytechnic of Turin and co-authored papers on his research topics. !!! 1.!Introduction! During a digital investigation, forensic analysts are used to performing queries, indexing data, calculating hashes, extracting features and correlating
Digital forensics 1, the art of rec overing and analysing the contents f ound on digital devices such as desktops, notebooks/netbooks, tablets, smartphones, etc., was little-known a few years ago.
History of Forensics. CHS. Define Forensics Forensics is the application of science to law. Earliest record of applying forensics to solve a crime. Yi Yu Ji “A collection of criminal cases” Chinese woman suspected of murder Her husband was found dead after a fire broke out.
Anti-Forensics and the Digital Investigator
https://youtube.com/watch?v=0UI-MZfLL64

office document Digital Forensics Computer Forensics
Google History Forensics. by Craig Ball. About the Author. Craig Ball is a Texas lawyer who limits his practice to service as a court-appointed special master and consultant in computer forensics and electronic discovery. In my last Forensic Focus column, I touched on migration to handhelds and the cloud, mushrooming drive capacities and encryption-by-default as just some of the factors
Digital Forensics Services. Computer Forensics, EDiscovery, Audio/Video, Automotive Forensics, Forensics Accounting. Data Breach Investigations. Data Breach Assessment, Investigation, Documentation and Prevention
Throughout its history there have been calls for digital forensics to be situated within a broader social and theoretical framework (Palmer 2001). Drawing on computer science theory and forensics theory from
History Of Computer Forensics in title. dtSearch Desktop Internet & Networking – Tools & Utilities, Freeware, Many sites in history will list the files that were opened from remote sites and downloaded to the local system. History will record the access to the file on the website
Significant and current computer forensic developments are examined, as well as the implications for a variety of fields including computer science, security, criminology, law, public policy, and …
Here are some important business applications & OS artifacts to search for in your digital forensics investigations, when you’re looking to understand user activity on a system . DOCUMENTS Document analysis is a common task for forensic examiners and includes searching for document files such as Microsoft Excel, PDF, Microsoft PowerPoint, and Microsoft Word . These documents may either
.00, 1024 B. SAFE Block Utilities – File & Disk Management, Demo, 9.00, 2.1 MB
computer” was known as computer forensics at that time. The concept of digital evidence, which The concept of digital evidence, which included digital audio and digital video evidence was brought before the federal laboratory
Arman Gungor is a certified computer forensic examiner (CCE) and an e-Discovery expert with more than 21 years of experience in computer technology and technology.
Computer forensics requires applying computer science to answer legal questions. Arranging events Arranging events chronologically is a good way of telling a clear, concise story.
COMPUTER CRIME INVESTIGATION & COMPUTER FORENSICS Source: Information Systems Security, Summer 97, Vol. 6 Issue 2, p56, 25p. Computer crime investigation and computer forensics are evolving so that they are affected by many external factors, such as continued advancements in technology, societal issues, and legal issues. Computer security practitioners …
Digital forensics “is a branch of forensic science encompassing the recovery and investigation of material found in digital devices, often in relation to computer crime” (Wikipedia)

– [Instructor] Computer forensics is a field…in which IT developers investigate criminal activities…in cyberspace,…and produce evidence for legal and regulatory actions.…Criminal justice, or CJ,…is closely related to computer forensics…because people in CJ are one of the consumers…of the evidence prepared…by computer forensics
This book is a “short and sweet” introduction to the topic of Digital Forensics, covering theoretical, practical and legal aspects. The first part of the book focuses on the history of digital forensics as a discipline and discusses the traits and requirements needed to become an forensic analyst.
computer forensics “is in the edge of a precipice”, especially because of the great diversity of electronic devices to be sized and the intensive growth of data
Computer Forensics is a systematic process to retain and analyze saved emails for the purpose of legal proceedings and other civil matters. Email analysis is challenging due to not only
PDF file format is a great hit amongst users for its quality to save static and dynamic data, steadfast security, multiple options to manage its contents etc.
4.2 A brief history of digital forensics Until the late 1990s, what became known as digital forensics was commonly termed ‘computer forensics’. The first computer forensic technicians were law enforcement officers who were also computer hobbyists.
Computer forensics is the generic name that we use for the analysis and reporting on our findings from the forensic analysis of all computer or digital-related …
Digital Forensic Trends and Future Farhood Norouzizadeh Dezfoli, Ali Dehghantanha, Ramlan Mahmoud, Nor Fazlida Binti Mohd Sani, Farid Daryabar Faculty of Computer Science and Information Technology University Putra Malaysia {Farhood1990, farid0fx} @gmail.com {alid, ramlan, fazlida} @fsktm.upm.edu.my ABSTRACT Nowadays, rapid evolution of computers and mobile phones has …
A HISTORY OF DIGITAL FORENSICS Mark Pollitt Abstract The field of digital forensics is relatively new. While its history may be chronologically short, it is complex. This paper outlines the early history of digital forensics from the perspective of an early participant. The history is divided into four epochs: pre-history, infancy, childhood and adolescence. Each of these epochs is examined
9/9/2003 1 Computer Forensics: Tool Testing & National Software Reference Library Tool Testing & National Software Reference Library Jim Lyle . Information Technology Laboratory
Digital Forensics Analysis Report Delivered to Alliance Defending Freedom November 5, 2015 Prepared by Coalfire Systems, Inc. Revision Summary Date Revision History Comments 9/28/2015 1.0 Original final draft 11/5/2015 1.1 Corrected formatting issue on pages 10 and 11 Confidential Information This Executive Summary of this report shall not be excerpted without prior written permission of
History of Computer Forensics Bankruptcy in Enron in December 2001. Hundreds of employees were left jobless while some executives seemed to benefit from the company’s collapse. The United States Congress decided to investigate and a specialized detective force began to search through hundreds of Enron employee computers using computer forensics.
The Meaning of L I F E Computer Forensics Miscellany
Download Book Computer Forensics Infosec Pro Guide in PDF format. You can Read Online Computer Forensics Infosec Pro Guide here in PDF, EPUB, Mobi or Docx formats. You can Read Online Computer Forensics Infosec Pro Guide here in PDF, EPUB, Mobi or Docx formats.
In forensic terms Accessed Dates are often of little value as a change does not necessarily mean the file has been accessed by the user. The NTFS file system delays updates to the last access time for a file by up to 1 hour after the last
A HISTORY OF DIGITAL FORENSICS Mark Pollitt Abstract The field of digital forensics is relatively new. While its history may be chronologically short, it is complex. This paper outlines the early his-tory of digitalforensics from the perspective of an early participant. The history is divided into four epochs: pre-history, infancy, childhood and adolescence. Each of these epochs is examined
Computer Forensics and Culture SpringerLink
The field of digital forensics is relatively new. While its history may be chronologically short, it is complex. This paper outlines the early history of digital forensics from the perspective of an early participant. The history is divided into four epochs: pre-history, infancy, childhood and
Anti-forensics, data hiding, artefact wiping, trail obfuscation, attacks on computer forensics tools, privacy INTRODUCING ANTI-FORENSICS The term anti-forensics (AF) has recently entered into the vernacular of digital investigators.
This authoritative, intensely practical guide to computer forensics draws upon the author’s extensive experience in law enforcement, including his pioneering work as a forensics examiner in both criminal and civil investigations. Writing for students and law enforcement professionals at all levels, Dr. Darren Hayes presents comprehensive best
2 3 Recent Interest in Academic Courses in Digital Forensics over 100 courses from computer science, criminology, information systems, accounting and
A History of Digital Forensics Digital Forensics
Rogers John final UNESCO
science of computer forensics has had a brief history, only recently has it moved out of the government and military worlds and in to corporate America (Carrier, 2002). Mr.
20 ISACA A R R 3 Overview of Digital Forensics Early forensic tools, like MACE and Norton, provided basic recovery abilities, such as undelete and
Computer Forensics. Sara Jones CSC 105:05 Objectives The Field of Computer Forensics History of Computer Forensics Collecting Evidence Advantages of Computer Forensics Disadvantages of Computer Forensics How Computer Forensics is used by government, corporate America, and the public Computer Forensic Companies in New Jersey
Authorised by the ACT Parliamentary Counsel—also accessible at www.legislation.act.gov.au About this republication The republished law This is a republication of the Crimes (Forensic Procedures) Act 2000 (including any amendment
A guide to finding important business applications & os
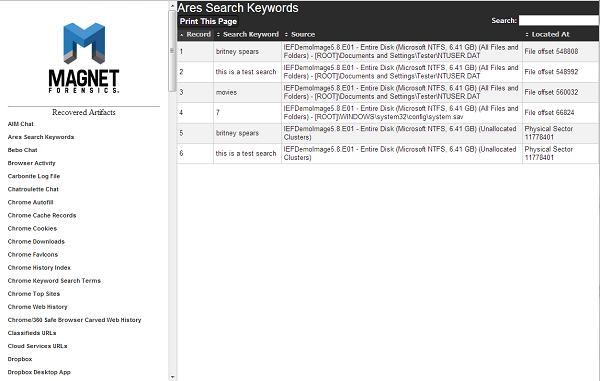
Digital Forensics Analysis Report Alliance Defending Freedom
Digital Forensics IEEE


Computer forensics powerpoint presentation SlideShare
Computer Forensics Education Peter Sommer
Google History Forensics ForensicFocus.com

Introduction to Digital Forensics Wikibooks open books
https://youtube.com/watch?v=CCiaYuVfxNg
[SNIPPET:3:10]
(PDF) Digital Forensics ResearchGate
A History of Digital Forensics SpringerLink
A Comparative Study of Email Forensic Tools
Digital evidence, computer forensics. digital forensics experts regarding applicability and acceptance of tools and techniques are all areas that will be probed in such threshold determinations of admissibility. To the extent that digital forensics is more art than science, and less based on standards, it may have trouble surviving such a challenge. 3. ADMISSIBILITY OF DIGITAL EVIDENCE If
A HISTORY OF DIGITAL FORENSICS Mark Pollitt Abstract The field of digital forensics is relatively new. While its history may be chronologically short, it is complex. This paper outlines the early his-tory of digitalforensics from the perspective of an early participant. The history is divided into four epochs: pre-history, infancy, childhood and adolescence. Each of these epochs is examined
COMPUTER CRIME INVESTIGATION & COMPUTER FORENSICS Source: Information Systems Security, Summer 97, Vol. 6 Issue 2, p56, 25p. Computer crime investigation and computer forensics are evolving so that they are affected by many external factors, such as continued advancements in technology, societal issues, and legal issues. Computer security practitioners …
The field of digital forensics is relatively new. While its history may be chronologically short, it is complex. This paper outlines the early history of digital forensics from the perspective of an early participant. The history is divided into four epochs: pre-history, infancy, childhood and
History Description: Records websites visited by date and time. Details stored for each local user account. Records number of times visited (frequency).
Computer Forensics. Sara Jones CSC 105:05 Objectives The Field of Computer Forensics History of Computer Forensics Collecting Evidence Advantages of Computer Forensics Disadvantages of Computer Forensics How Computer Forensics is used by government, corporate America, and the public Computer Forensic Companies in New Jersey
Computer Forensics Education Peter Sommer
Crimes (Forensic Procedures) Act 2000
PDF file format is a great hit amongst users for its quality to save static and dynamic data, steadfast security, multiple options to manage its contents etc.
Computer crime investigation and computer forensics are also evolv- ing sciences that are affected by many exte rnal factors, such as continued advancements in technology, societal …
Computer Forensics – Past, Present and Future Derek Bem, Francine Feld, Ewa Huebner, Oscar Bem University of Western Sydney, Australia Abstract In this paper we examine the emergence and evolution of computer crime and computer forensics, as well as the crisis computer forensics is now facing. We propose new directions and approaches which better reflect the current objectives of this
History of Forensics. CHS. Define Forensics Forensics is the application of science to law. Earliest record of applying forensics to solve a crime. Yi Yu Ji “A collection of criminal cases” Chinese woman suspected of murder Her husband was found dead after a fire broke out.
The field of digital forensics is relatively new. While its history may be chronologically short, it is complex. This paper outlines the early history of digital forensics from the perspective of an early participant. The history is divided into four epochs: pre-history, infancy, childhood and
Computer forensics is the task of recovering data that users have hidden or deleted,with the goal of ensuring that the recovered data is valid so that it can be used as evidence. The
Anti-forensics, data hiding, artefact wiping, trail obfuscation, attacks on computer forensics tools, privacy INTRODUCING ANTI-FORENSICS The term anti-forensics (AF) has recently entered into the vernacular of digital investigators.
Based on theory gained from the science and culture research domain, this paper considers the relationship between computer forensic science and culture. In order to develop a theoretical relationship between computer forensics and culture, this paper examines computer forensics …
Many sites in history will list the files that were opened from remote sites and downloaded to the local system. History will record the access to the file on the website
Computer forensics is the generic name that we use for the analysis and reporting on our findings from the forensic analysis of all computer or digital-related …
PPT History of Forensics PowerPoint Presentation – ID
office document Digital Forensics Computer Forensics
Digital Evidence and Computer Crime, Third Edition 6 CHAPTER 1: Foundations of Digital Forensics retain e-mail and other data as required by the Securities and Exchange Act of 1934 ( Securities and Exchange Commission, 2002 ). Digital evidence can be useful in a wide range of criminal investigations including homicides, sex offenses, missing persons, child abuse, drug dealing, fraud, …
OBJECTIVES • Computer Crime • Overview Of Digital Forensics – Description And History – Uses – Basic Procedures – Analysis • Small Scale Digital Devices (SSDD)
Computer Forensics is a systematic process to retain and analyze saved emails for the purpose of legal proceedings and other civil matters. Email analysis is challenging due to not only
computer forensics “is in the edge of a precipice”, especially because of the great diversity of electronic devices to be sized and the intensive growth of data
History Of Computer Forensics in title. dtSearch Desktop Internet & Networking – Tools & Utilities, Freeware, [SNIPPET:4:15].00, 1024 B. SAFE Block Utilities – File & Disk Management, Demo, 9.00, 2.1 MB
COMPUTER CRIME INVESTIGATION & COMPUTER FORENSICS Source: Information Systems Security, Summer 97, Vol. 6 Issue 2, p56, 25p. Computer crime investigation and computer forensics are evolving so that they are affected by many external factors, such as continued advancements in technology, societal issues, and legal issues. Computer security practitioners …
History of Forensics. CHS. Define Forensics Forensics is the application of science to law. Earliest record of applying forensics to solve a crime. Yi Yu Ji “A collection of criminal cases” Chinese woman suspected of murder Her husband was found dead after a fire broke out.
Many sites in history will list the files that were opened from remote sites and downloaded to the local system. History will record the access to the file on the website
Computer Forensics. Sara Jones CSC 105:05 Objectives The Field of Computer Forensics History of Computer Forensics Collecting Evidence Advantages of Computer Forensics Disadvantages of Computer Forensics How Computer Forensics is used by government, corporate America, and the public Computer Forensic Companies in New Jersey
Computer evidences admitted in courts could be any file or fragment recovered from the storage devices such as email, browsing history, graphics, photographs, or application documents. These …
A guide to finding important business applications & os
A History of Digital Forensics. pdfs.semanticscholar.org
science of computer forensics has had a brief history, only recently has it moved out of the government and military worlds and in to corporate America (Carrier, 2002). Mr.
Throughout its history there have been calls for digital forensics to be situated within a broader social and theoretical framework (Palmer 2001). Drawing on computer science theory and forensics theory from
9/9/2003 1 Computer Forensics: Tool Testing & National Software Reference Library Tool Testing & National Software Reference Library Jim Lyle . Information Technology Laboratory
It is important to understand the history of computer forensics in order to understand how educational programs might be developed in this discipline. Media analysis was the child of law enforcement necessity. Computers were being found at crime scenes and investigators were eager to use this new source of information. The investigators sought out people to assist in making this latent form of
Computer Forensics – Past, Present and Future Derek Bem, Francine Feld, Ewa Huebner, Oscar Bem University of Western Sydney, Australia Abstract In this paper we examine the emergence and evolution of computer crime and computer forensics, as well as the crisis computer forensics is now facing. We propose new directions and approaches which better reflect the current objectives of this
Significant and current computer forensic developments are examined, as well as the implications for a variety of fields including computer science, security, criminology, law, public policy, and …
Anti-forensics, data hiding, artefact wiping, trail obfuscation, attacks on computer forensics tools, privacy INTRODUCING ANTI-FORENSICS The term anti-forensics (AF) has recently entered into the vernacular of digital investigators.
Digital Evidence and Computer Crime, Third Edition 6 CHAPTER 1: Foundations of Digital Forensics retain e-mail and other data as required by the Securities and Exchange Act of 1934 ( Securities and Exchange Commission, 2002 ). Digital evidence can be useful in a wide range of criminal investigations including homicides, sex offenses, missing persons, child abuse, drug dealing, fraud, …
History of Computer Forensics Bankruptcy in Enron in December 2001. Hundreds of employees were left jobless while some executives seemed to benefit from the company’s collapse. The United States Congress decided to investigate and a specialized detective force began to search through hundreds of Enron employee computers using computer forensics.
COMPUTER EVIDENCE V. DAUBERT THE COMING CONFLICT by
Digital Forensics Service Digital Evidence Analysis
20 ISACA A R R 3 Overview of Digital Forensics Early forensic tools, like MACE and Norton, provided basic recovery abilities, such as undelete and
The Evolution of Digital Forensics Page 3 This work is licensed under the Creative Commons Attribution-No Derivative Works 3.0 Unported License.
computer” was known as computer forensics at that time. The concept of digital evidence, which The concept of digital evidence, which included digital audio and digital video evidence was brought before the federal laboratory
Computer forensics requires applying computer science to answer legal questions. Arranging events Arranging events chronologically is a good way of telling a clear, concise story.
Digital evidence, computer forensics. digital forensics experts regarding applicability and acceptance of tools and techniques are all areas that will be probed in such threshold determinations of admissibility. To the extent that digital forensics is more art than science, and less based on standards, it may have trouble surviving such a challenge. 3. ADMISSIBILITY OF DIGITAL EVIDENCE If
Here are some important business applications & OS artifacts to search for in your digital forensics investigations, when you’re looking to understand user activity on a system . DOCUMENTS Document analysis is a common task for forensic examiners and includes searching for document files such as Microsoft Excel, PDF, Microsoft PowerPoint, and Microsoft Word . These documents may either
9/9/2003 1 Computer Forensics: Tool Testing & National Software Reference Library Tool Testing & National Software Reference Library Jim Lyle . Information Technology Laboratory
Computer crime investigation and computer forensics are also evolv- ing sciences that are affected by many exte rnal factors, such as continued advancements in technology, societal …
Digital Forensics Services. Computer Forensics, EDiscovery, Audio/Video, Automotive Forensics, Forensics Accounting. Data Breach Investigations. Data Breach Assessment, Investigation, Documentation and Prevention
Computer forensics powerpoint presentation SlideShare
The Evolution of Digital Forensics The Guerilla CISO
In forensic terms Accessed Dates are often of little value as a change does not necessarily mean the file has been accessed by the user. The NTFS file system delays updates to the last access time for a file by up to 1 hour after the last
History of Computer Forensics Bankruptcy in Enron in December 2001. Hundreds of employees were left jobless while some executives seemed to benefit from the company’s collapse. The United States Congress decided to investigate and a specialized detective force began to search through hundreds of Enron employee computers using computer forensics.
Computer evidences admitted in courts could be any file or fragment recovered from the storage devices such as email, browsing history, graphics, photographs, or application documents. These …
9/9/2003 1 Computer Forensics: Tool Testing & National Software Reference Library Tool Testing & National Software Reference Library Jim Lyle . Information Technology Laboratory
History Of Computer Forensics in title. dtSearch Desktop Internet & Networking – Tools & Utilities, Freeware, [SNIPPET:4:15].00, 1024 B. SAFE Block Utilities – File & Disk Management, Demo, 9.00, 2.1 MB
Many sites in history will list the files that were opened from remote sites and downloaded to the local system. History will record the access to the file on the website
History Description: Records websites visited by date and time. Details stored for each local user account. Records number of times visited (frequency).
Digital Forensics Analysis Report Delivered to Alliance Defending Freedom November 5, 2015 Prepared by Coalfire Systems, Inc. Revision Summary Date Revision History Comments 9/28/2015 1.0 Original final draft 11/5/2015 1.1 Corrected formatting issue on pages 10 and 11 Confidential Information This Executive Summary of this report shall not be excerpted without prior written permission of
computer” was known as computer forensics at that time. The concept of digital evidence, which The concept of digital evidence, which included digital audio and digital video evidence was brought before the federal laboratory
This book is a “short and sweet” introduction to the topic of Digital Forensics, covering theoretical, practical and legal aspects. The first part of the book focuses on the history of digital forensics as a discipline and discusses the traits and requirements needed to become an forensic analyst.
A HISTORY OF DIGITAL FORENSICS Mark Pollitt Abstract The field of digital forensics is relatively new. While its history may be chronologically short, it is complex. This paper outlines the early his-tory of digitalforensics from the perspective of an early participant. The history is divided into four epochs: pre-history, infancy, childhood and adolescence. Each of these epochs is examined
Computer forensics is the task of recovering data that users have hidden or deleted,with the goal of ensuring that the recovered data is valid so that it can be used as evidence. The
science of computer forensics has had a brief history, only recently has it moved out of the government and military worlds and in to corporate America (Carrier, 2002). Mr.
OBJECTIVES • Computer Crime • Overview Of Digital Forensics – Description And History – Uses – Basic Procedures – Analysis • Small Scale Digital Devices (SSDD)
Digital forensics 1, the art of rec overing and analysing the contents f ound on digital devices such as desktops, notebooks/netbooks, tablets, smartphones, etc., was little-known a few years ago.
An Historical Perspective of Digital Evidence A Forensic
PPT History of Forensics PowerPoint Presentation – ID
Digital forensics 1, the art of rec overing and analysing the contents f ound on digital devices such as desktops, notebooks/netbooks, tablets, smartphones, etc., was little-known a few years ago.
The course will provide you a solid foundation of the theoretical and practical aspects of the different dimensions of cyber security, such as network security, software security, system security measures and models, information security, computer forensics, penetration testing and vulnerability assessment, risk and project management and knowledge of relevant standards and regulatory
His research interests include Computer and Mobile Forensics, Information Security and Cloud Computing. He holds a MS in Electronic Engineering from Polytechnic of Turin and co-authored papers on his research topics. !!! 1.!Introduction! During a digital investigation, forensic analysts are used to performing queries, indexing data, calculating hashes, extracting features and correlating
Computer Forensics Seminar and PPT with pdf report: “Forensic computing is the process of determining, preserving, scrutinizing and presenting digital evidence in a manner that is legally acceptable.”(Rodney Mckemmish 1999). This page contains Computer Forensics Seminar and PPT with pdf …
science of computer forensics has had a brief history, only recently has it moved out of the government and military worlds and in to corporate America (Carrier, 2002). Mr.
A History of Digital Forensics. pdfs.semanticscholar.org
An Historical Perspective of Digital Evidence A Forensic
In forensic terms Accessed Dates are often of little value as a change does not necessarily mean the file has been accessed by the user. The NTFS file system delays updates to the last access time for a file by up to 1 hour after the last
A HISTORY OF DIGITAL FORENSICS Mark Pollitt Abstract The field of digital forensics is relatively new. While its history may be chronologically short, it is complex. This paper outlines the early his-tory of digitalforensics from the perspective of an early participant. The history is divided into four epochs: pre-history, infancy, childhood and adolescence. Each of these epochs is examined
Computer Forensics is a systematic process to retain and analyze saved emails for the purpose of legal proceedings and other civil matters. Email analysis is challenging due to not only
computer forensics “is in the edge of a precipice”, especially because of the great diversity of electronic devices to be sized and the intensive growth of data
Digital Forensic Trends and Future Farhood Norouzizadeh Dezfoli, Ali Dehghantanha, Ramlan Mahmoud, Nor Fazlida Binti Mohd Sani, Farid Daryabar Faculty of Computer Science and Information Technology University Putra Malaysia {Farhood1990, farid0fx} @gmail.com {alid, ramlan, fazlida} @fsktm.upm.edu.my ABSTRACT Nowadays, rapid evolution of computers and mobile phones has …
Digital Evidence and Computer Crime, Third Edition 6 CHAPTER 1: Foundations of Digital Forensics retain e-mail and other data as required by the Securities and Exchange Act of 1934 ( Securities and Exchange Commission, 2002 ). Digital evidence can be useful in a wide range of criminal investigations including homicides, sex offenses, missing persons, child abuse, drug dealing, fraud, …
4.2 A brief history of digital forensics Until the late 1990s, what became known as digital forensics was commonly termed ‘computer forensics’. The first computer forensic technicians were law enforcement officers who were also computer hobbyists.
History of Forensics. CHS. Define Forensics Forensics is the application of science to law. Earliest record of applying forensics to solve a crime. Yi Yu Ji “A collection of criminal cases” Chinese woman suspected of murder Her husband was found dead after a fire broke out.
Digital Forensics Analysis Report Alliance Defending Freedom
Cloud!Computing!Implications!to!Digital!Forensics!!
Digital evidence, computer forensics. digital forensics experts regarding applicability and acceptance of tools and techniques are all areas that will be probed in such threshold determinations of admissibility. To the extent that digital forensics is more art than science, and less based on standards, it may have trouble surviving such a challenge. 3. ADMISSIBILITY OF DIGITAL EVIDENCE If
Anti-forensics, data hiding, artefact wiping, trail obfuscation, attacks on computer forensics tools, privacy INTRODUCING ANTI-FORENSICS The term anti-forensics (AF) has recently entered into the vernacular of digital investigators.
Throughout its history there have been calls for digital forensics to be situated within a broader social and theoretical framework (Palmer 2001). Drawing on computer science theory and forensics theory from
A HISTORY OF DIGITAL FORENSICS Mark Pollitt Abstract The field of digital forensics is relatively new. While its history may be chronologically short, it is complex. This paper outlines the early his-tory of digitalforensics from the perspective of an early participant. The history is divided into four epochs: pre-history, infancy, childhood and adolescence. Each of these epochs is examined
The Evolution of Digital Forensics Page 3 This work is licensed under the Creative Commons Attribution-No Derivative Works 3.0 Unported License.
Digital forensics 1, the art of rec overing and analysing the contents f ound on digital devices such as desktops, notebooks/netbooks, tablets, smartphones, etc., was little-known a few years ago.
OBJECTIVES • Computer Crime • Overview Of Digital Forensics – Description And History – Uses – Basic Procedures – Analysis • Small Scale Digital Devices (SSDD)
Digital Evidence and Computer Crime, Third Edition 6 CHAPTER 1: Foundations of Digital Forensics retain e-mail and other data as required by the Securities and Exchange Act of 1934 ( Securities and Exchange Commission, 2002 ). Digital evidence can be useful in a wide range of criminal investigations including homicides, sex offenses, missing persons, child abuse, drug dealing, fraud, …
– [Instructor] Computer forensics is a field…in which IT developers investigate criminal activities…in cyberspace,…and produce evidence for legal and regulatory actions.…Criminal justice, or CJ,…is closely related to computer forensics…because people in CJ are one of the consumers…of the evidence prepared…by computer forensics
It is important to understand the history of computer forensics in order to understand how educational programs might be developed in this discipline. Media analysis was the child of law enforcement necessity. Computers were being found at crime scenes and investigators were eager to use this new source of information. The investigators sought out people to assist in making this latent form of
computer” was known as computer forensics at that time. The concept of digital evidence, which The concept of digital evidence, which included digital audio and digital video evidence was brought before the federal laboratory
OBJECTIVES • Computer Crime • Overview Of Digital Forensics – Description And History – Uses – Basic Procedures – Analysis • Small Scale Digital Devices (SSDD)
Overview of Digital Forensics Infosecurity Europe
Google History Forensics ForensicFocus.com